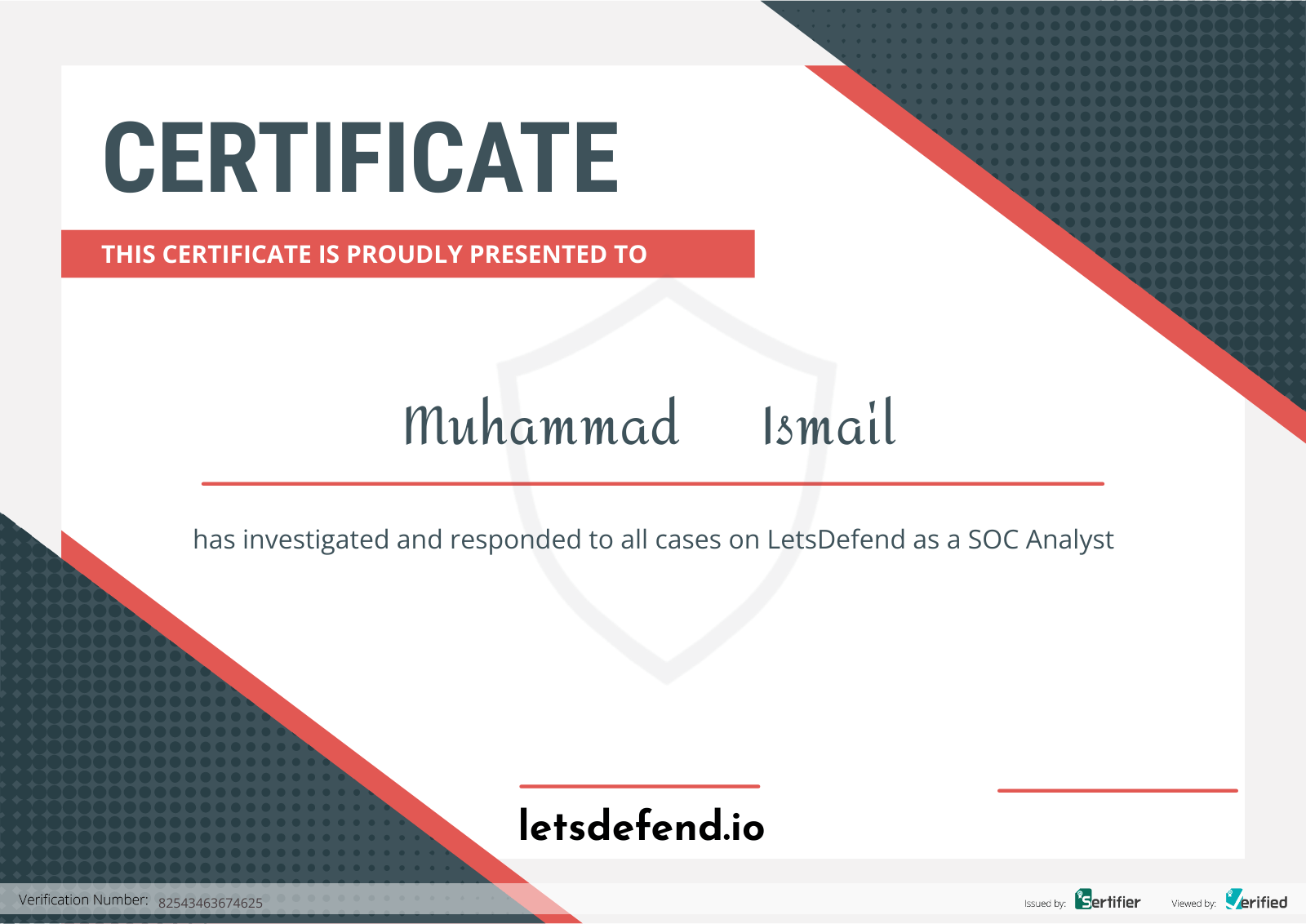
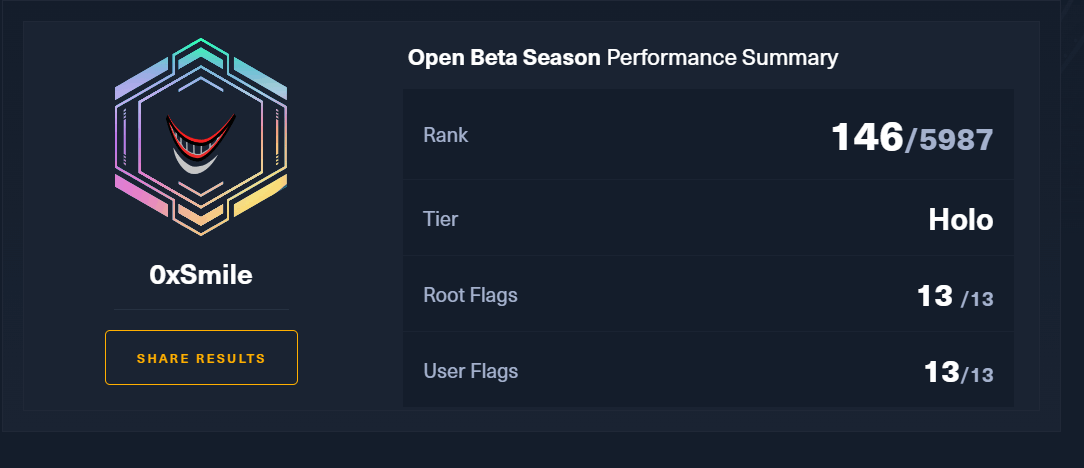
Hey , I'm Muhammad Ismail Ramzan 👋
I'm deeply passionate about cybersecurity and graduated in the field. I'm fascinated by technology, particularly the advancements AI brings to the cybersecurity realm. Dive into my blog where you can learn something new today!😊 I'm also quite social, so feel free to get in touch with me anytime.